When a major online platform, say like a social media service people use every single day, suddenly becomes slow or even stops working, it can feel rather confusing, can't it? People might wonder what's going on, especially if they rely on it for staying connected or getting their news. Sometimes, this kind of disruption comes from something called a "DDoS" attack, which is essentially a way to make a system too busy to function properly.
This idea of overwhelming a system is, in a way, like trying to fit too many people through a single small doorway all at once; nobody gets through very quickly, or perhaps at all. For a place like Twitter, which handles millions upon millions of interactions every second, even a slight slowdown can feel like a huge problem for its users. It’s a bit of a big deal, actually, when these things happen, because so much of our daily communication relies on these digital spaces staying open and responsive.
So, when we talk about something like a DDoS attack affecting a service that lets you share short messages with the world, we're really talking about a significant challenge to its ability to serve its users. It's about how these digital disruptions can make a difference in how we interact online, and what goes into keeping these large platforms running smoothly. We'll be looking into some of the ways these attacks operate and why they can be quite difficult to manage, you know, for those who are trying to keep things secure.
Table of Contents
- What Does It Mean When Systems Get Overloaded?
- Is Messing with Computer Systems Really Against the Rules?
- How Do Many Computers Make a Big Problem?
- What Are Botnets and Why Are They a Challenge for DDoS Twitter?
What Does It Mean When Systems Get Overloaded?
When we talk about a system becoming overloaded, especially in the context of something like a DDoS, we are describing a situation where a computer or a network connection gets so much incoming activity that it just can't keep up. It's a bit like a popular restaurant suddenly getting every table filled at the same exact moment, with everyone wanting to order and pay all at once. The kitchen and the waitstaff would simply be overwhelmed, and service would grind to a halt. In the digital world, this means websites might not load, messages might not send, or, you know, your favorite social media site could just stop responding. This kind of disruption can feel quite frustrating for anyone trying to use the service.
The goal of these attacks is to make a service unavailable to its real users. They achieve this by sending an enormous amount of fake traffic, essentially clogging up the digital pathways. Imagine a very wide highway, but then suddenly, countless vehicles, maybe even millions of them, all try to enter the highway at the same time through one single on-ramp. No one would get anywhere, and the whole system would be stuck. That, in some respects, is what happens when a digital service is hit by an attack that aims to flood its capacity. It's a very direct way to make something stop working as it should, and it can cause a lot of headaches for the people who manage these services.
This method of disruption isn't about breaking into a system to steal information; it's purely about stopping it from working. It's a different kind of digital mischief, focusing on making things inaccessible rather than gaining entry. For example, if you wanted to make sure no one could post an update or see what their friends are doing on a platform like Twitter, an attack of this sort would be the way to go about it. It’s a pretty blunt instrument, in a way, but it can be quite effective at causing widespread annoyance and disruption for a lot of people who depend on that service for their daily interactions.
Learning About How DDoS Twitter Works
When people talk about tools that let you simulate a DDoS, it's often for a very specific reason: education. These tools are put together so that folks who are learning about computer security can get a hands-on feel for how these attacks happen. It’s like a practice exercise for someone who wants to understand how to build a strong fence by first learning how someone might try to push it over. You get to see the mechanics of the attack, how the traffic flows, and what happens when a system gets too much information all at once. This kind of learning helps security professionals figure out how to protect platforms, perhaps even a service like Twitter, from real-world incidents, you know, before they actually occur.
The idea is to understand the vulnerabilities, the weak spots, without actually causing any harm. So, these scripts are built with the intention of being used in a controlled environment, a sort of digital sandbox where you can experiment without affecting anyone else's computer or online experience. It's a safe way to explore a serious topic. Knowing how these attacks are put together helps people who work to keep systems safe. They can then build better defenses and put up stronger protections against future problems. This kind of knowledge is pretty essential, actually, for anyone involved in keeping our online world running smoothly and securely, especially for big public platforms like Twitter.
By simulating these events, people gain a deeper insight into the kind of pressures a system might face. They can observe how different parts of a network respond under strain and identify where the weak points might be. This is a crucial step for anyone who wants to work in cybersecurity, as it gives them a practical sense of what they're up against. Without these kinds of learning opportunities, it would be much harder to prepare for the challenges that come with defending large online services, including, you know, the systems that keep platforms like Twitter up and running for everyone. It's about learning to build a better shield by understanding the sword.
Is Messing with Computer Systems Really Against the Rules?
It's super important to remember that while learning about these things is valuable, actually using these tools to disrupt someone else's computer system is a very serious matter. It's not just a prank; it's something that can have real legal consequences. Most places have laws that make it quite clear that interfering with computer systems without permission is against the rules. This means that if you were to use a tool meant for learning to actually try and overload a real website or service, you could face some pretty severe penalties. It's a bit like learning to drive a car, but then taking it for a joyride on a busy street without a license and causing an accident; there are clear boundaries, and crossing them has consequences, you know, for everyone involved.
These laws are in place to protect everyone who uses the internet. They're there to make sure that online services can operate without fear of being shut down by malicious actions. So, when someone creates a script for educational purposes, there's always a very clear warning that it should never, ever be used for anything that could be considered an actual attack. The line between learning and doing something illegal is very distinct, and it's something that people need to be very aware of. It's a bit like how a doctor learns about diseases; they study them to heal people, not to make them sick. The intent behind using these tools makes all the difference, and it's a very important distinction to keep in mind, actually.
Breaking these rules can lead to all sorts of trouble, including fines, time in jail, or both. It’s not a small thing, and the authorities take it very seriously. The damage caused by these kinds of disruptions can be quite extensive, affecting businesses, individuals, and even public services. So, while the curiosity to see how these things work is understandable, the proper and ethical use of such knowledge is absolutely essential. It’s about respecting the digital space we all share and ensuring that it remains a place where people can connect and share information without fear of disruption. This applies to any online service, including, say, a place where people share their thoughts like Twitter, which needs to be kept safe for all its users.
The Serious Side of DDoS Twitter Simulations
Thinking about how a service like Twitter might experience issues, it's worth noting that problems similar to what a DDoS attack can cause have popped up for various platforms in the past. For instance, there was a situation some years ago, around 2018, where a particular piece of internet infrastructure, something called HAProxy, might have been involved in some service interruptions. While we're not saying that was a DDoS on Twitter specifically, it does highlight how parts of the internet's underlying structure can sometimes face challenges that lead to widespread issues. It just goes to show, you know, how sensitive these large systems can be to unexpected pressure.
The point here is that even a small weakness in a widely used piece of software or equipment can, in a way, have a ripple effect across many different services. This is why security experts are constantly working to find and fix potential vulnerabilities before they can be exploited. They're always looking for ways to make the internet a more stable and reliable place for everyone. It’s a bit of a never-ending task, actually, because as technology changes, so do the ways people might try to cause problems. This ongoing effort is what helps keep big platforms, perhaps like Twitter, running smoothly most of the time, even when facing potential digital storms.
Understanding these historical incidents, even if they are just general examples of system strain, helps us appreciate the constant vigilance required to maintain online stability. It shows that the digital world isn't always perfectly calm, and that there are always folks working behind the scenes to keep things from going wrong. So, when we talk about the potential for something like a DDoS to affect a platform, it’s not just theoretical; it’s based on the very real challenges that online services, including perhaps even a platform like Twitter, have had to deal with at various points in time. It's about learning from the past to protect the future, you know, in a digital sense.
How Do Many Computers Make a Big Problem?
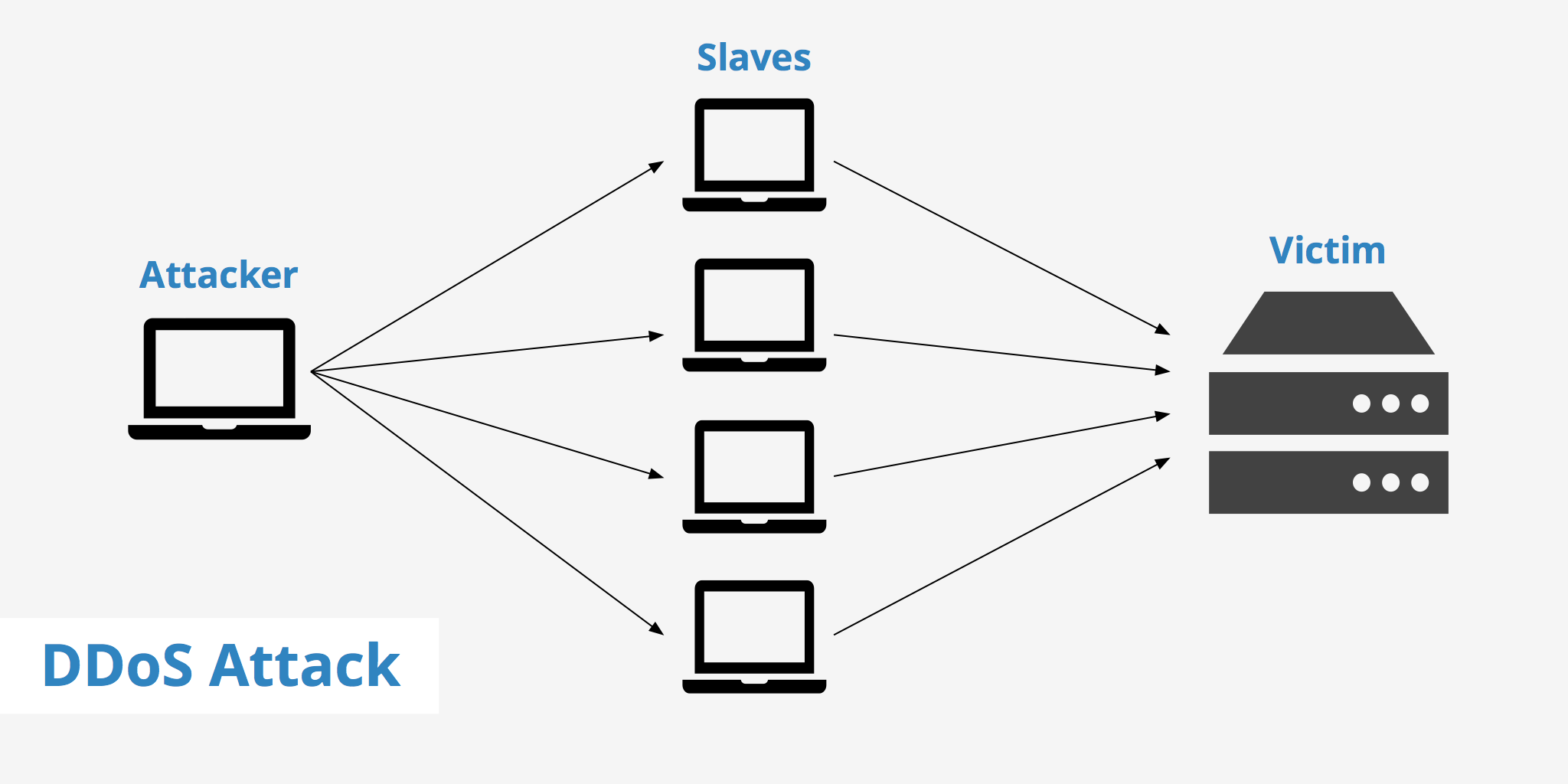
The effectiveness of a DDoS attack comes from a very simple idea: strength in numbers. Instead of one computer trying to overwhelm a system, which would probably be easy to stop, these attacks use a huge number of separate computer systems all at once. Imagine trying to block a single person from entering a building; that’s pretty simple. But what if hundreds, or even thousands, of people suddenly tried to push their way in at the same exact moment? It would be nearly impossible to stop them all. That, in some respects, is how a DDoS attack works, using many compromised machines to create an overwhelming flood of bad traffic. It’s a very clever, if rather destructive, approach to digital disruption.
These individual computers, which are often regular people's machines that have been taken over without their knowledge, act as sources for the attack. They all send requests or information to the target at the same time, creating a massive amount of digital noise. This noise makes it impossible for the target system to tell the difference between real users and the attack traffic. It’s a bit like trying to have a conversation in a stadium where everyone is yelling at the top of their lungs; you just can’t hear anything important. This collective action is what makes these attacks so difficult to defend against, because the incoming requests appear to be coming from so many different places, you know, all at once.
The sheer volume of this traffic is what causes the trouble. It fills up all the available pathways, overloads the processing power of the target's servers, and basically makes the service unusable for anyone trying to get through. It’s not about finding a single weak spot; it’s about simply overwhelming everything. This method is very different from other types of digital attacks that might try to sneak in quietly or steal information. This one is all about making a lot of noise and creating chaos. It’s a pretty direct way to cause disruption, and it can be quite effective at making a system like, say, a social media platform like Twitter, completely unreachable for its users. It's a brute force approach, in a way.
The Power of Many in a DDoS Twitter Scenario
When we think about the many sources that can contribute to a DDoS attack, it's not just limited to personal computers. The sources of this attack traffic can include a wide range of connected devices and network resources. This means that anything from smart home devices, security cameras, or even things like digital video recorders that are connected to the internet could, in some cases, be unknowingly used as part of an attack. It's a pretty broad scope, actually, for what can be pulled into these kinds of disruptions. The internet of things, as it's sometimes called, presents a lot of potential points for these kinds of issues to arise, you know, without people even realizing it.
Even things like servers that are part of search engines, or other large network resources, could potentially be used if they are somehow compromised. The idea is that any device with an internet connection that can be controlled by an attacker can become a part of this digital army. This makes it very hard to identify and block all the incoming bad traffic, because it’s coming from so many different types of machines spread across the globe. It’s a bit like trying to stop a rainstorm by catching every single raindrop; it’s just not practical when there are so many of them. This wide variety of sources adds a significant layer of difficulty for those trying to defend against these attacks, especially for a large, globally distributed service like Twitter.
The more varied the sources, the more challenging it becomes to filter out the malicious activity from the legitimate user traffic. This diversity in attack sources means that security teams have to be incredibly adaptable in their defense strategies. They can’t just block one type of device or one specific location; they have to be ready for anything. This ongoing challenge means that platforms that handle a lot of traffic, perhaps even a service like Twitter, are always working to improve their defenses. It’s a constant race between those who want to cause disruption and those who want to keep services running smoothly for everyone, you know, all the time.
What Are Botnets and Why Are They a Challenge for DDoS Twitter?
Most of the software used for carrying out DDoS attacks today relies on something called "botnets." A botnet is basically a collection of internet-connected devices, each running one or more "bots," which are essentially automated programs. These bots have been installed on the devices without the owners' knowledge, often through various sneaky methods like tricking someone into clicking a bad link or exploiting a weakness in their device's security. Once a device is part of a botnet, it can be controlled remotely by the person who created the botnet, allowing them to coordinate a massive attack. It’s a bit like building an army of unwitting digital soldiers, all ready to follow commands, you know, without question.
The reason botnets are so effective for DDoS attacks is that they allow the attacker to send traffic from a huge number of different computers, each with its own unique internet address, or IP address. If an attack came from just one machine, it would be relatively easy for a service provider to simply block that single IP address, and the problem would be solved. But when the attack comes from thousands or even millions of different IP addresses, blocking them all becomes an incredibly difficult, almost impossible, task. It’s a bit like trying to play a game of whack-a-mole where there are too many moles popping up all at once, and you can’t hit them all. This distributed nature is what makes botnet-driven DDoS attacks such a persistent headache for those trying to keep online services running.
This wide distribution of attack sources makes it very hard for security systems to distinguish between legitimate users and the malicious traffic. The sheer volume and variety of the incoming connections can quickly overwhelm even the most robust defenses. It means that the people responsible for keeping platforms like Twitter online have to employ very sophisticated methods to identify and filter out the bad traffic without accidentally blocking real users. They might use complex algorithms or specialized hardware to try and sort through the digital noise. It's a continuous effort to stay ahead of the methods used by those who want to cause disruption, because the techniques used by attackers are always, you know, evolving.
The challenge of dealing with botnets is that they are constantly shifting. New devices can be added to the network, and the command structure can change, making it difficult to pinpoint the source of the control. This adaptability means that a defense strategy that worked yesterday might not be as effective today. So, for any large online service, including a platform that lets you share thoughts like Twitter, protecting against these kinds of attacks requires constant vigilance and adaptation. It’s a bit like playing a never-ending game of chess, where your opponent is always coming up with new moves. This ongoing battle highlights the complex nature of keeping our digital world safe and accessible for everyone who uses it, you know, every day.
So, to sum up, we've talked about how scripts can help people learn about DDoS attacks in a safe way, emphasizing that using them for real disruptions is against the rules and has serious consequences. We looked at how past issues with internet infrastructure, like the one involving HAProxy in 2018, show how vulnerable systems can be. We also discussed how DDoS attacks get their power from many compromised computers acting together, and why modern DDoS software often uses vast networks of these machines, called botnets, to make attacks incredibly difficult to stop compared to just one source.
- Aaliyah Milan
- Deepika Padukone Twitter
- Lori Dawkins Twitter
- Ianandmariah Twitter
- Carter Cameron Twitter